OWS Network Requirements
Network Requirements and Allowlist
Ports TCP 80 and TCP 443 are utilized by default for each address unless otherwise specified. On highly secure networks, TCP port 443 can be used exclusively for communication [HTTPS/TLS].
NOTE: OpenEye Web Services (OWS) domains list MarkMonitor as the Registrar and AWSDNS name servers.
|
THESE LOCATIONS ARE REQUIRED
THESE LOCATIONS ARE REQUIRED FOR SOFTWARE UPDATES, VIDEO CLIP EXPORTS AND THUMBNAIL IMAGES IN REPORTS/ALERTS (TCP 443 ONLY)
|
THESE LOCATIONS ARE REQUIRED FOR OS & SOFTWARE UPDATES
THESE LOCATIONS ARE REQUIRED FOR POS CONNECT
THESE LOCATIONS ARE OPTIONAL
|
Ensuring Remote Access through OpenEye Web Services
OpenEye Web Services utilizes a video relay system that does not require port forwarding, thereby reducing maintenance and complexity. While no additional network configuration should be required, some specific ports cannot be blocked for outgoing traffic.
In order to ensure the successful commissioning of your OpenEye Web Services enabled recorder, the following ports must not be blocked:
Incoming
- None required
Outgoing (these ports do not need to be forwarded, but cannot be blocked)
- TCP port 443 (used for OWS relay)
Content Filtering
In some cases, menus and interfaces will load properly and all setup elements are accessible, but Live and Search video never appear. This problem likely stems from content filtering (also known as ‘media inspection’ on some devices). When a firewall or proxy is configured to filter content, the system will attempt to wait until the entire file has been received before examining it, as identified by the 'end of file' marker contained in the video stream data. However, when streaming video from a recorder, the data does not have an 'end of file' marker, so the system holds the video indefinitely while waiting for the marker.
OpenEye recommends that installers review their content filtering options and refer to the allowlist section for details on URLs to exclude from the filter.
Allowlist Requirements
Network Allowlist Requirements
If the network is preventing the recorder from communicating with OWS, it will prevent the service from making the necessary connection required for authenticating the recorder. This will require a Network Administrator to allowlist the hosts that the recorder will reach out to in order to make a connection to OWS.
NOTE: We recommend adding the domains as documented below to your network allowlist instead of the IP address the domains resolve to. If your network filter uses reverse DNS, it is recommended to add your recorder to an exclusion range that is not filtered as our IP range will resolve to amazonaws.com.
NOTE: Communication with the relay service u5fgb.com uses a payload of message/http. This is an embedded HTTP response message from the recorder to the client software. If your network filter is blocking traffic to u5fgb.com you must allow “Content-Type” of “message/http” in your network filter.
Ports TCP 80 and TCP 443 are utilized by default for each address unless otherwise specified. On highly secure networks, TCP port 443 can be used exclusively for communication [HTTPS/TLS].
The following locations are required for everyone:
*.*.u5fgb.com (for communication with relay service)
NOTE: Trusting all traffic from u5fgb.com will allow communication to current relay services and new relay services as they become available.
restapi.gp4f.com and *.api.gp4f.com (for communication with API services and branding portal)
- TCP 443 only
activateapi.gp4.com (For communication with licensing service)
- TCP 443 only
ows.openeye.net (for OWS login portal)
- TCP 443 only
assist.dvrsupportcenter.com (for temporary Remote Assist Session initiated by Technical Support)
- TCP 443 only
supportlink.gp4f.com (for communication with Support tools such as Remote Assist Session, Reboot, and Device Log Export)
- TCP 443 only
serverupdates.net (for Microsoft Windows Updates (WSUS)
- TCP 8531 only
ctldl.windowsupdate.com (for Certification Validation - required when installing/updating recorder server software)
- TCP 80 and 443
stun.u5fgb.com (for peer to peer connections to improve performance)
- UDP 3478
The following locations are required for software updates, video clip exports and thumbnail images in reports/alerts (TCP 443 for all):
oe-prod-devmon.s3.us-west-2.amazonaws.com
oe-prod-files.s3.us-west-2.amazonaws.com
oe-prod-media.s3.us-west-2.amazonaws.com
The following locations are required for POS Connect (TCP 443 for all):
oe-cpos1.gp4f.com
The following locations are optional:
*.openeye.net and *.gp4f.com (for support of future enhancements)
- TCP 443 only
1.cctv.pool.ntp.org (for support of NTP (Network Time Server)
- UDP 123 only
NOTE: Cisco Iron Port devices may need a “Cisco Data Security” policy setup to allow POST traffic through. This will resolve issues with live video showing black when using relay.
Email Allowlist Requirements
When using an email service that filters emails based on a allowlist, it is possible that communication from OWS will be blocked. Configuring your email server allowlist to accept incoming emails from OWS servers will prevent missed communication from OWS.
The following servers are required:
Bandwidth Requirements
OpenEye recommends an NVR site upload bandwidth speed of 5 Mbps for an optimal experience when remotely viewing video over the WAN (Internet). This will result in a positive user experience when reviewing video from one 4MP high definition stream, or up to 9 standard definition streams. In instances where less than 5 Mbps is available remote users should plan to utilize standard definition streams for retrieving video over the WAN.
While the OWS platform is highly configurable to meet exact bandwidth usage requirements the following table may be referenced as a typical use case:
| Average bandwidth usage based on D1/4MP, 4,000Kbps, 15 IPS, 30 GOP IP Cameras | ||
| Channel Count | Live & Search SD Playback | Live & Search HD Playback |
| Single channel | 800 Kbps | 4 Mbps |
| 4 channel grid | 3 Mbps | 16 Mbps |
| 9 channel grid | 7 Mbps | 36 Mbps |
| 16 channel grid | 13 Mbps | 64 Mbps |
NOTE: The OWS platform dynamically chooses HD or SD streams for viewing based on the client display configuration selected by the user. For example, a 4-channel view will deliver SD video by default while a single-channel view will automatically deliver the HD stream. Stream selection may also be manually controlled using the stream selection control at the top of the applicable display screen.
Recorder Data Usage
OpenEye recorders always maintain a lightweight connection to OWS. OpenEye recommends a weekly configuration backup, alert transmissions of recorder health, and day/night images for cameras. Alert images attached to video events is optional.
While the OWS platform is highly configurable to meet exact data usage requirements the following table may be referenced as a typical use case:
| Data Usage based on minimum one image per alert per day / minimum one weekly config backup | ||
| Usage Category | Usage per 30 Days (MB) | Average per Day (MB) |
| Baseline Cloud Communication | 1350 | 45 |
| Configuration File Backup | .24 | .01 |
| Alert Transmission | .99 | .03 |
| Alert Images | 45 | 1.5 |
| Day / Night Images | 1440 | 48 |
| Estimated Total with All Options | 2836.23 | 94.54 |
| Export 20 mins. to OWS per month | |
| Usage Category | Usage per Clip (MB) |
| 20 Minute Incident Review (4MP to OWS) | 984 |
| 20 Minute Incident Backup (2MP to OWS) | 306 |
NOTE: Measurement of 20 minutes covers a 20 minute clip or multiple clips equaling up to 20 minutes.
NOTE: Video is downsized before export to 2MP. An option is available to keep at 4MP, but for more data usage.
NOTE: Once stored in OWS, review of incident clips in the cloud do not affect data usage of individual sites.
Connection Methods
In general, remote connection to your recorder can be established without any open ports or router configuration. The OpenEye Web Services negotiates both peer-to-peer and relay connections, meaning that nothing more than an internet connection is required.
OWS will first attempt to negotiate a peer-to-peer connection between the client and recorder. Using the relay service and a STUN server, the client and recorder attempt to negotiate a connection using outbound UDP ports. If successful, video will be transmitted via SCTP over UDP while metadata is relayed through secure OWS servers.
Under some circumstances, a peer-to-peer connection may fail to be established:
- If UDP traffic is being blocked by firewalls at either the client or recorder location
- If both the client or recorder locations make use of endpoint-dependent filtering
- If a device at either location uses endpoint-dependent mapping
If a P2P attempt fails, the remote client will seamlessly select to receive all video and metadata over the OWS video relay service.
If optimal performance is desired, connections can be configured using Direct Connect/LAN Smart Forwarding or Local IP Connection. In both cases, inbound ports will need to be opened.
Local IP Connection: TCP ports 80 (HTTP) or 443 (HTTPS) are needed to connect via Command Station OE Mobile, and the thin client.
Direct Connect/LAN Smart Forwarding: To connect via Command Station, OE Mobile, and the thin client, TCP port 80 will need to be opened.
Connection Types and Port Requirements
Inbound and outbound port requirements are listed below by connection and application type along with brief explanations of each.
Relay
Video streaming performance is typically best when video is sent directly from the recorder to the client. When the client initiates a connection through OWS, the client attempts to connect directly to the recorder using STUN. If this succeeds, then a direct video connection is established; if not, the connection will automatically fall back to the Relay method.
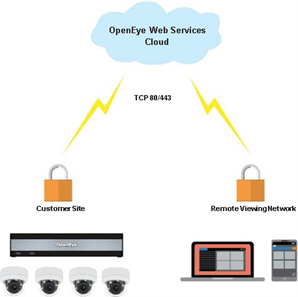
For the Command Station Desktop Client, OpenEye Mobile Apps, and the Cloud Web Client or Apex Web Client, no inbound ports are needed as long as a persistent OWS/Recorder connection has been established.
NOTE: While no ports need to be opened, blocking outbound traffic on TCP port 80 or 443 will cause a relay connection to fail.
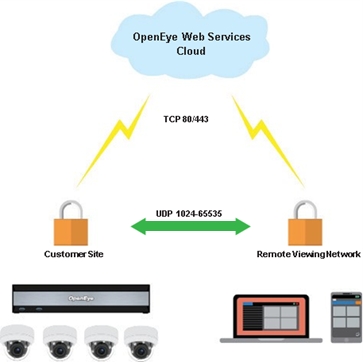
Peer-to-Peer
Peer-to-Peer connections are optional but will provide improved performance over-utilizing the relay service. A Peer-to-Peer connection utilizes one random UDP port per connection in the 1024-65535 range (incoming and outgoing). If UDP is unconditionally blocked in either direction on any ports within the range, Peer-to-Peer will be unreliable, or not work at all. Additionally, locking down (i.e. blocking outgoing UDP traffic) on all but one port will not succeed because OpenEye Web Services relies on dynamic per-session UDP port mapping. If Peer-to-Peer fails, you will automatically fall back to the Relay method.
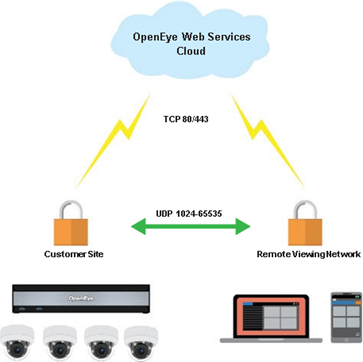
For the Command Station Desktop Client, OpenEye Mobile Apps, and the Apex Web Client, no inbound ports are needed as long as persistent OWS/Recorder connection has been established.
NOTE: While no ports need to be opened, blocking outbound traffic on TCP port 80 or 443 and UDP ports 1024 – 65535 will cause a P2P connection to fail.
WebRTC
OpenEye Web Services (OWS) Cloud Video Player has been updated to support WebRTC, a plugin free, real time video transmission layer that allows direct video connection from a recorder to the remote cloud client for improved security and reduced latency. WebRTC is capable of establishing a LAN connection for video transmission, depending on a user’s network configuration, but unlike LAN Smart Forwarding a local connection cannot be guaranteed in all conditions. The release of WebRTC support in the cloud-based web client represents OpenEye’s ongoing commitment to continuously improving security and performance for our users.
LAN Smart Forwarding
LAN Smart Forwarding is a feature of OpenEye Web Services that will keep most traffic within a local network when both the client and the recorder are on the same network. When the client initiates a connection to a recorder through OWS, the external IP addresses of the client and recorder are provided to OWS. If they match, OWS will instruct the client application to connect directly to the recorder using the local IP Address. Even in a large corporate environment with multiple subnets, you can configure IP ranges to allow LAN Smart Forwarding to acknowledge that both the client and the recorder still reside on the same network.
You can enable LAN Smart Forwarding within OpenEye Web Services under Recorder Management, then select the desired recorder, and Remote Network Settings. This feature is enabled by default for new recorders added to OWS.
Direct Connect
While most users find the performance of the previously discussed connection methods acceptable, users wishing to achieve the absolute best video streaming performance will want to consider using Direct Connect. Direct Connect allows you to specify an IP address for clients to use when connecting
to the recorder. By using an external IP address or URL, and forwarding the following ports to the recorder, you will connect directly to the recorder in all cases using your OWS credentials.
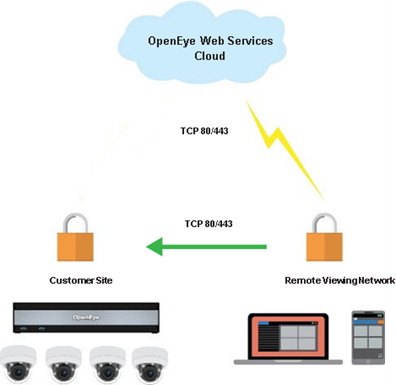
Incoming (this port is required and needs to be opened and forwarded to the recorder)
- TCP port 80 (used for Command Station Desktop Client, OpenEye Mobile Apps, and the Apex Web Client.
NOTE: TCP port 80 is used by default, but HTTPS via TCP port 443 can be set up for Direct Connect by entering https://<ipaddress> in IP Address or Domain field.
Once the recorder is configured you can enable Direct Connect within OpenEye Web Services under Recorder Management, Recorders, then select the desired recorder, and select Remote Network Settings. You can enter the IP address (or Domain) and the port to ensure OpenEye Web Services uses a direct connection.
OWS Proxy Server Support
OpenEye Web Services supports the use of network proxy services to securely aggregate HTTP communication in corporate environments. OWS requires an HTTP 1.1 compliant proxy that does not require additional authentication.
NOTE: Depending on the OWS connection method, some performance latency may be incurred. Relayed connections will route all video traffic through the proxy host, while a peer-to-peer negotiated connection, if available, will deliver video directly from the recorder to the client. Control messages will remain routed through the proxy.
Port Technical Information
Technical information is listed in two ways: ports used and connection method.
Ports Used
Recorder: Incoming
- TCP port 80
- TCP port 2001
- Used for DMP Intrustion Panel events
- TCP port 443
Recorder: Outgoing
- TCP port 80
- Used for OWS relay service
- TCP port 443
- Used for OWS relay service
- UDP port 3478
- Used to connect to the STUN server
Web Services Peer to Peer Connection
- UDP ports in the 1024-65535 range (incoming and outgoing) need to remain unblocked (specifically opening them is not required)
- Once a connection is made to the STUN server, a single random port is used on both the client and DVR. This is used to send and receive video when connecting peer to peer.
- NOTE: The following may vary depending on the firewall:
- If UDP is unconditionally blocked in either direction on any ports within the range, peer to peer will work unreliably or not at all.
- If the firewall is configured to allow all outgoing UDP traffic and stateful incoming UDP traffic, peer to peer will most likely work.
Connection Method
OWS - Direct Connect / LAN Smart Forwarding
- Command Station Desktop Client:
- TCP port 80
- TCP port 443
- OpenEye Mobile Apps:
- TCP port 80
- TCP port 443
- Apex Web Client:
- TCP port 80
- TCP port 443
NOTE: TCP port 80 is used by default, but HTTPS via TCP port 443 can be set up for Direct Connect by entering https://<ipaddress> in IP Address or Domain field.
OWS - Relay
- Command Station Desktop Client:
- No Inbound Ports needed as long as an OWS/Recorder connection is already established.
- OpenEye Mobile Apps:
- No Inbound Ports needed as long as an OWS/Recorder connection is already established.
- Apex or Cloud Web Client:
- No Inbound Ports needed as long as an OWS/Recorder connection is already established.
NOTE: While no ports need to be opened, blocking outbound traffic on TCP port 80 or 443 will cause a relay connection to fail.
OWS - Peer to Peer
- Command Station Desktop Client:
- No Inbound Ports needed as long as an OWS/Recorder connection is already established.
- 1024-65535 – Outbound UDP
- OpenEye Mobile Apps:
- No Inbound Ports needed as long as an OWS/Recorder connection is already established.
- 1024-65535 – Outbound UDP
- Apex Web Client:
- No Inbound Ports needed as long as an OWS/Recorder connection is already established.
- 1024-65535 – Outbound UDP
NOTE: While no ports need to be opened, blocking outbound traffic on TCP port 80 or 443 and UDP ports 1024 – 65535 will cause a P2P connection to fail.
Local IP Connection
- Command Station:
- TCP port 80
- TCP port 443
- OpenEye Mobile Apps:
- TCP port 80
- TCP port 443
- Apex Web Client:
- TCP port 80
- TCP port 443
Ports Used
| Destination | ||||||
| Apex Server | OWS Cloud | Apex Web Client | Desktop Client | Mobile Apps | ||
| Source | Apex Server |
80/TCP 443/TCP 3478/UDP |
80/TCP 443/TCP |
80/TCP 443/TCP |
80/TCP 443/TCP |
|
| OWS Cloud | ||||||
| Apex Web Client |
80/TCP 443/TCP |
|||||
| Desktop Client |
80/TCP 443/TCP |
|||||
| Mobile Apps |
80/TCP 443/TCP |
|||||
